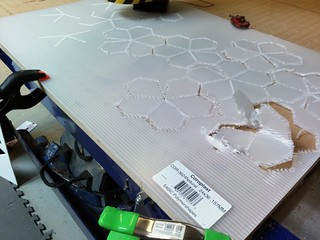
THe Gosper Curve is a self-similar fractal that can be turned into a visually interesting, yet very difficult puzzle on the laser cutter. With all of the pieces the same color it is nearly impossible, but a bi-color version is a doable challenge. You can move the slices (in blue in the SVG file) around to vary the puzzle or change the difficulty; the current version has lots of very similar pieces to make it full of “garden paths” that require frequent back-tracking when the solution almost works.

More details are posted on trmm.net/Fractal_Puzzle and the design files are thing:2204078 on thingiverse.